- Cloud
- Networks
- Linux
- Innovation
•
•
•
Tactile Internet: The role of QoS in teleoperation systems
Touch is increasingly being recognized as a modality that will complement hearing and vision as a third media stream over the Internet in various future haptic applications, enabling full immersion and significantly impacting society in many ways.
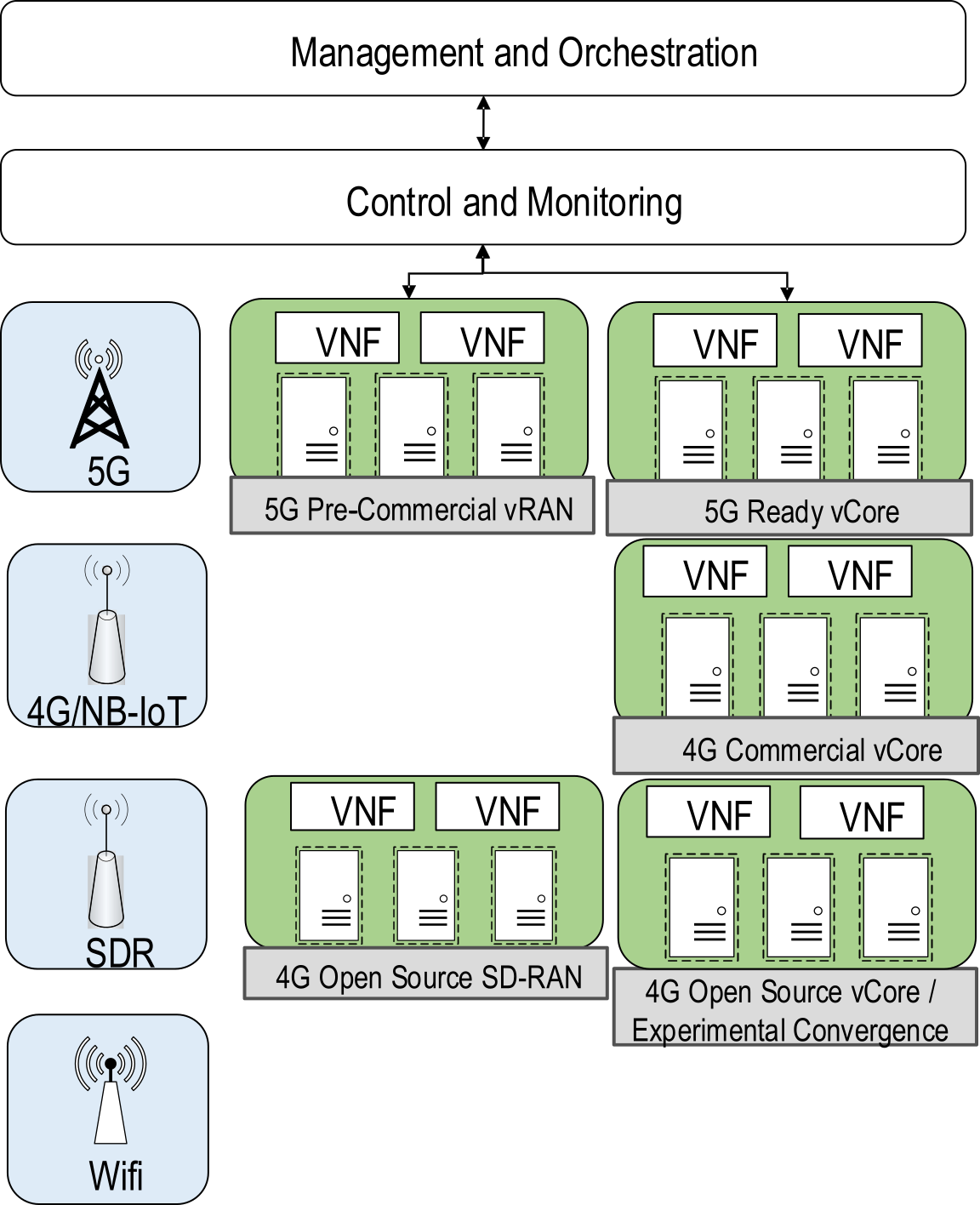
Cloud Computing meets 5G
Nowadays, many 5G components can be virtualized and they can run in cloud environments. In the 5G radio access and core networks, hardware and software are becoming clearly separated from each other [1]. It means that 5G features are virtualized in software and delivered over commodity hardware where it runs as virtual machines or containers in private or public cloud environments.
What is a Light Virtual Access Point (LVAP)?
Wireless networks are widely used in areas such as business centres, airports, university campuses or even in many city areas. Light Virtual Access Point (LVAP) are a solution for coordinating Wi-Fi access points.

General architecture for Software Defined Networking (SDN)
The terminology and layered architecture for SDN systems has been defined by the Software Defined Networking Research Group (SDNRG) of the Internet Research Task Force (IRTF) in [1]. Although it is not intended to standardize any layer or interface, it provides a reference for approaches that can be followed when defining SDN architectures.

How to setup a Kubernetes cluster
A tutorial on how to setup a Kubernetes cluster using a Ubutu 16.04 virtuam machine. At the end of this tutorial, you will have a kubernetes cluster that consist of one Kubernetes master and two Kubernetes nodes.

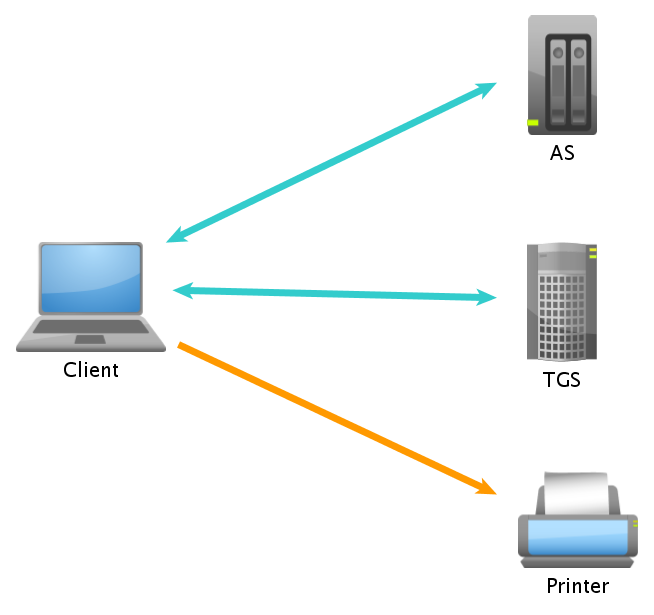
Kerberos protocol operation
The authentication protocol Kerberos allows a number of computers to prove their identity among them safely over an insecure network. The operation of the protocol is based on the Needham-Schroeder protocol, which defines a ''trusted third party'' called Key Distribution Center (KDC).
How to modify files with SED?
Sed is a stream editor which is used to perform basic text transformations on an input stream (a file or input from a pipeline) or filter strings. It permits to modify the contents of different lines in a file, based on some parameters.

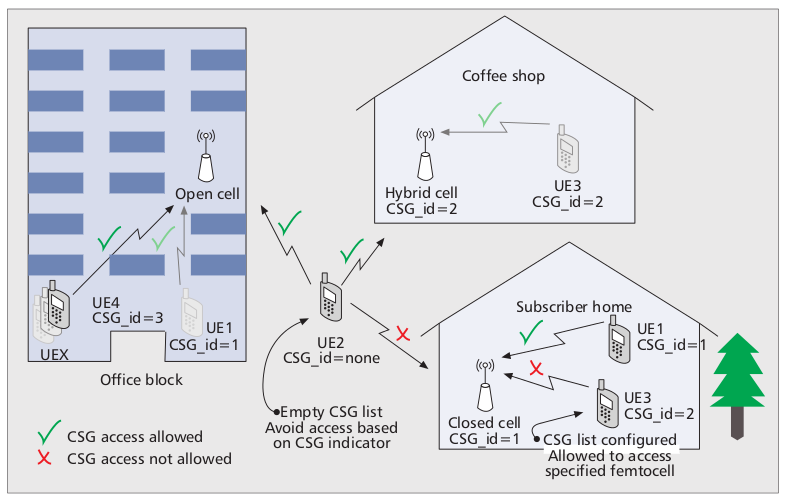
Femtocell's access methods
Femtocells basically have three different operating modes open access, closed access and a combination of both named hybrid access.
What is LaTeX?
Latex is a language for high quality editing documents, especially oriented to book composition, scientific and technical documents, that include formulas and high quality images. It consists on a set of Tex macros (one low-level language) and has become almost a standard for scientific publications in areas such as mathematics, physics and engineering, since we can have finer control over any typographical appearance of the document.
AES Other attacks
It is clear that so far, none of the attacks carried out against full-AES has been successful, these attacks usually focus on reducing rounds. Many authors claim that none of the following types of attacks have been more effective than an exhaustive-key search.
