- Cloud
- Networks
- Linux
- Innovation
•
•
•
Femto-cells others challenges in QoS managing
The transmission of a information packet over an IP network is susceptible to delays, so the femto-cell may experience problems for obtaining an immune base time to jitter. Operators should ensure the concept of QoS in Femto-cells, the parameters of these scenarios should be comparable to those offered by the macro-cells.

How to install SPAN?
Installation is very simple, for Linux and Mac users only need to have installed Tcl/Tk 8.5, then download SPAN software from here and unzip it. Finally, we define two environment variables SPAN and AVISPA_PACKAGE.
Femto-cell challenges in managing interferences
In this context, operators have deployed femto-cells systems in order to decrease the distance to the EU and to maintain good signal quality. However, femto-cells must operate in the designated band frequency for such communication and match to the assigned frequencies to the operator.
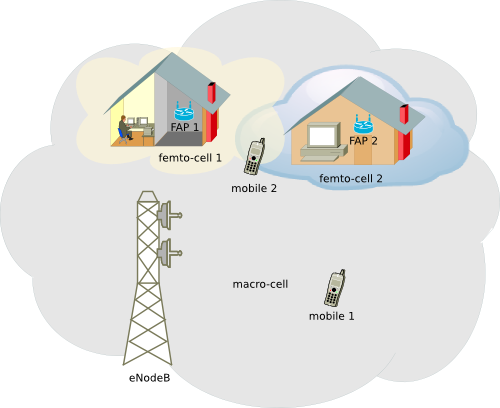
Applications for the development of scientific papers, data processing and simulation
Applications which facilitate the data processing when we need to work with research result, whether mathematical or network. Below, a list of useful applications for processing data from research, documents, images and other related management system is described.
How to manage groups, users and permissions?
Groups are useful for grouping a number of special permissions on the system to a group of users, each user must belong to at least one group. In any system there must be a superuser (root), which will have all the permits and maximum privileges allowing to do any work on the system.
Attack on AES Omission of MixColumns
A recent study by Orr Dunkelman and Nathan Keller shows that security can be compromised by the omission of such transformation. The results show that in the case of the analysis by omitting MixColumns, the algorithm complexity is reduced by a factor of 2^16.

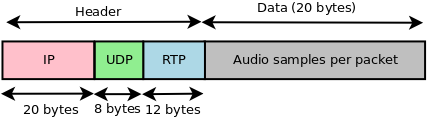
How to obtain a traffic model for VoIP?
In this article, we describe how to obtain a traffic model for VoIP which is quite easy to interpret and it provides some of the things that must be done.
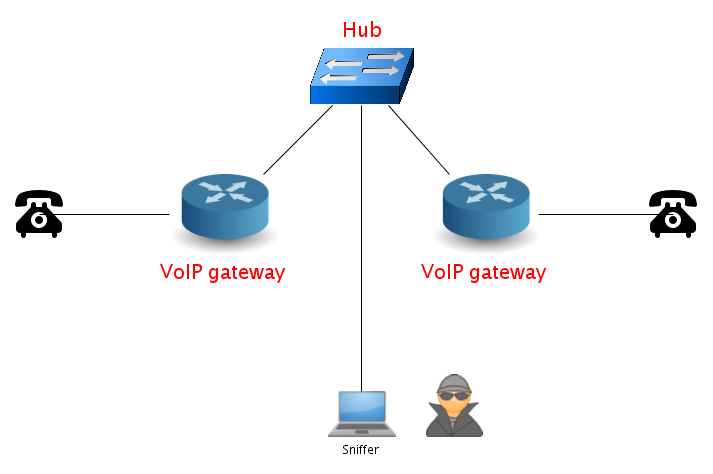
What is VoIP?
VoIP refers to the technology required for voice communication over IP, while ToIP is a telephone service for users, which uses VoIP technology to give such service. VoIP allows voice transmission via an IP network, including those connected to the Internet. It involves digitizing voice signals, via a codec.
Cryptographic attack on AES Impossible Differential Attack
Some time ago, I read an interesting article of a "successful attack" against AES, the famous symmetric-key algorithm. Raphael C.-W. Phan presented a seven rounds "impossible differential attack" for AES-192 and AES-256. Someone may ask what kind of attack is this?, well, it is a crypt-analysis that takes advantage of the differences that are impossible to be, in a data block through encryption, in order to discover the key?. Without going into many details of the method used, below I comment some of the most important results of this study.

How to install, update and other things with package managers in Linux?
Package managers are tools to automate the process of installing, upgrading, uninstalling or configuring software on Linux.
