- Cloud
- Networks
- Linux
- Innovation
•
•
•
AES (Advanced Encryption Standard) overview Part II
Now, we discuss some details of the so-called transformations (ByteSub, ShiftRow, MixColumns and AddRoundKey) and the subkey generation process. To see more details in a more dynamic way the Rijndael Animation application is recommended.
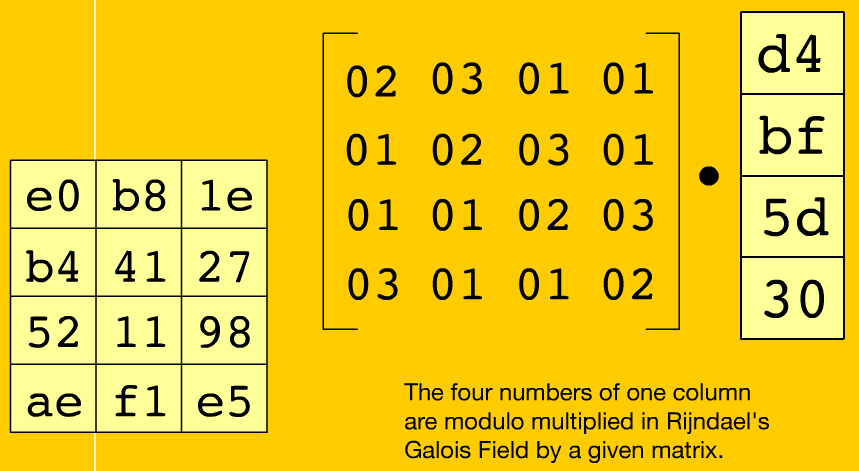
AES (Advanced Encryption Standard) Overview Part I
The AES (Advanced Encryption Standard) algorithm, known as Rijndael, was so-named by its creators Joan Daemen and Vincent Rijmen, it is the current international standard for communications encryption since october 2000. This algorithm is characterized by a symmetric block cipher with variable key length, the default key length is 128 bits but can also be set to 192 or 256 bits.

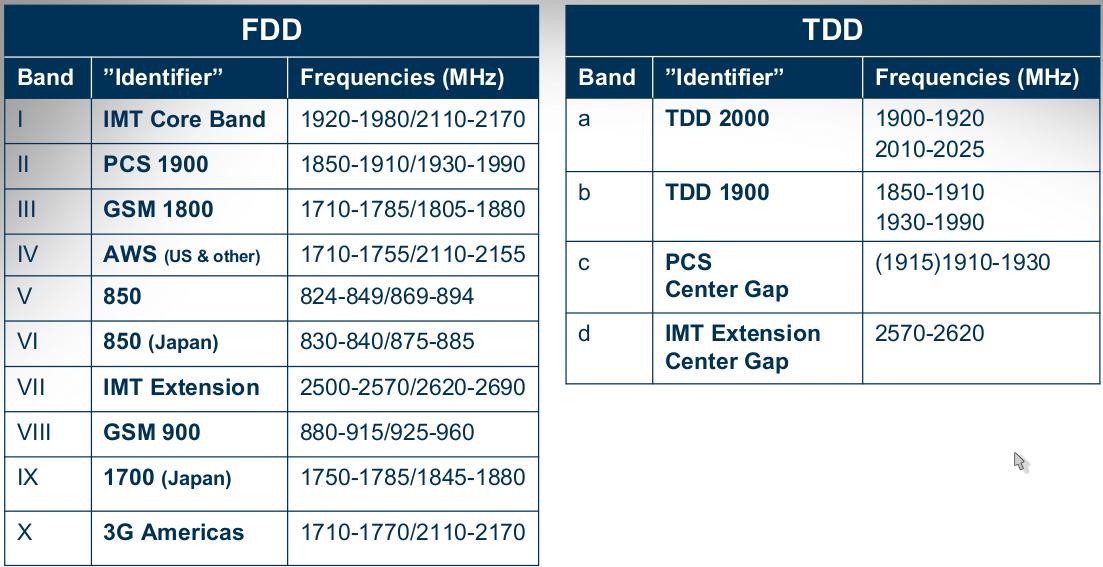
LTE data transmission techniques
Duplex Systems transmission LTE-FDD and LTE-TDD. FDD (Frequency Division Duplex) is a scheme of transmitting and receiving signals, this system allows full duplex communication using two different frequencies. TDD (Time Division Duplex) is another multiplexing technique for communication that uses a single channel or frequency, for information transmission. The modulation technique and channel coding is one of the important points of the LTE speed ranges. This new model of mobile network uses AMC (Adaptive Modulation and Coding)
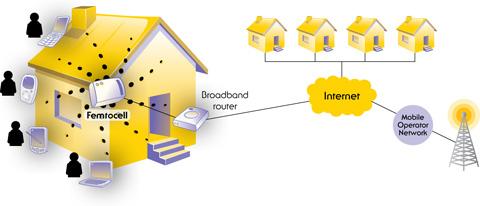
Macrocells and femtocells Interaction
Macro-cells are not very efficient in the residential area due to penetration problems that have been mentioned in a previous article, also in the macro-cells there are many users and is more difficult to provide QoS to all of them. For these reasons Internet Service Providers (ISP) have opted for femto-cell implementation at residential level, in order to increase the quality of services provided.
The spectrum and multiplexing in LTE
Regarding the spectrum, LTE becomes quite flexible, allowing bandwidths of 1.25MHz, 1.6MHz, 2.5MHz, 5MHz, 10MHz, 15MHz and 20MHz in the downlink and uplink. Furthermore, it supports broadcast transmission in downlink and uplink-downlink modes, on the other hand, radio resources for broadcast transmissions can be modified according to the operator needs. Orthogonal Frequency Division Multiplexing (OFDM) is a frequency multiplexing scheme characterized by sending a certain amount of carrier frequencies in a specified bandwidth, each of these carriers, transports information using modulation schemes such as QAM or PSK (QPSK, 16QAM and 64QAM). One of the main advantages of this type of multiplexing is about the fading of signals, delays and in general against interference, also has excellent characteristics against multipath. Furthermore, with QAM and PSK modulations is possible to transmit more amount symbols per cycle.

Quality of Service end-to-end in femto-cells environments
From the point of view of LTE management, it is permitted to define profiles and classes of services, which are key points when negotiating QoS mobile requirements during the communication establishment, the transit of packets, even in handovers. However, it is necessary to consider the access and transport network if we want to ensure end-to-end QoS. The access network should have clearly configured the types of services, traffic types, among others, by suitably adjusting parameters, that define the modulation and coding schemes, maximum latency, jitter, guaranteed minimum bandwidth, allowed delay, and other parameters that technology allows to adapt depending on the service type we access.
The two pillars of a symmetric-key algorithm
In order to consider a symmetric-key algorithm robust and safe, it is necessary to have been subjected to analysis by the scientific community in this area, so they could give evidence that it is immune to most known attacks. In general, we can say that this type of algorithms must consider two fundamental pillars

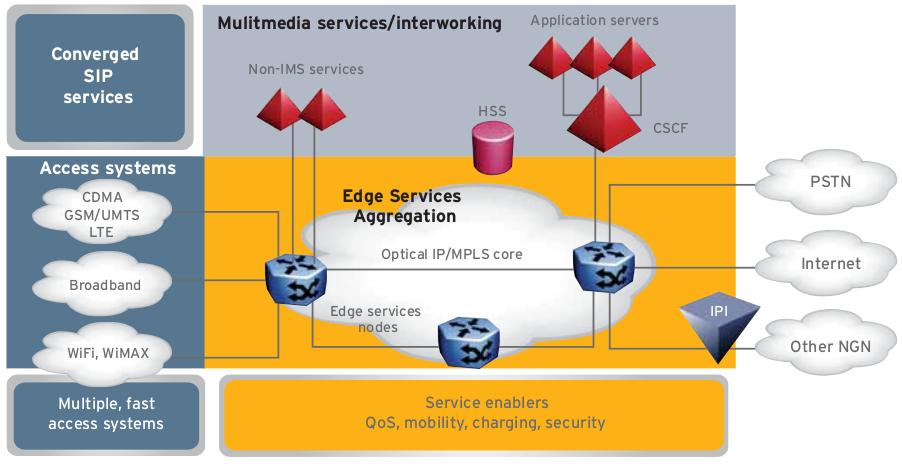
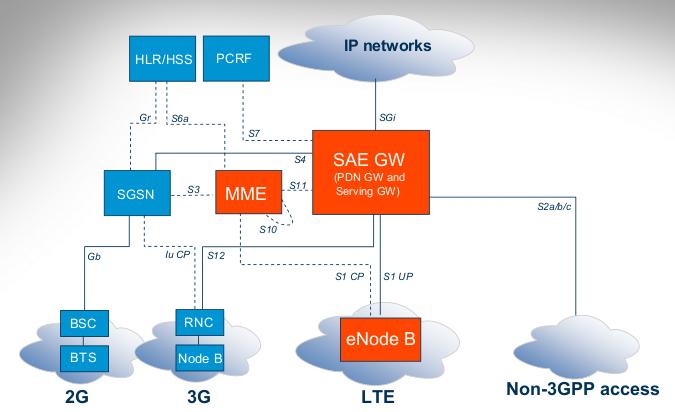
Architecture Features LTE / SAE
The fourth generation mobile (4G), it is very common that we like to be updated, we care about general aspects of the architecture of this new technology. Well, "System Architecture Evolution" (SAE) or also known as EPC ("Evolved Packed Core") has its development from the year 2004 until 2009, during that time many studies have been deployed which allowed to define the standards that describes the architecture of the core network.
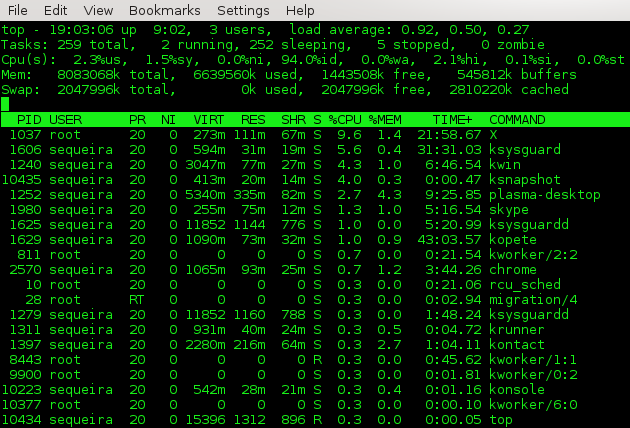
Useful commands for system information and manage sesion
In this case, several commands are presented which allow us to collect certain system information and session managing.
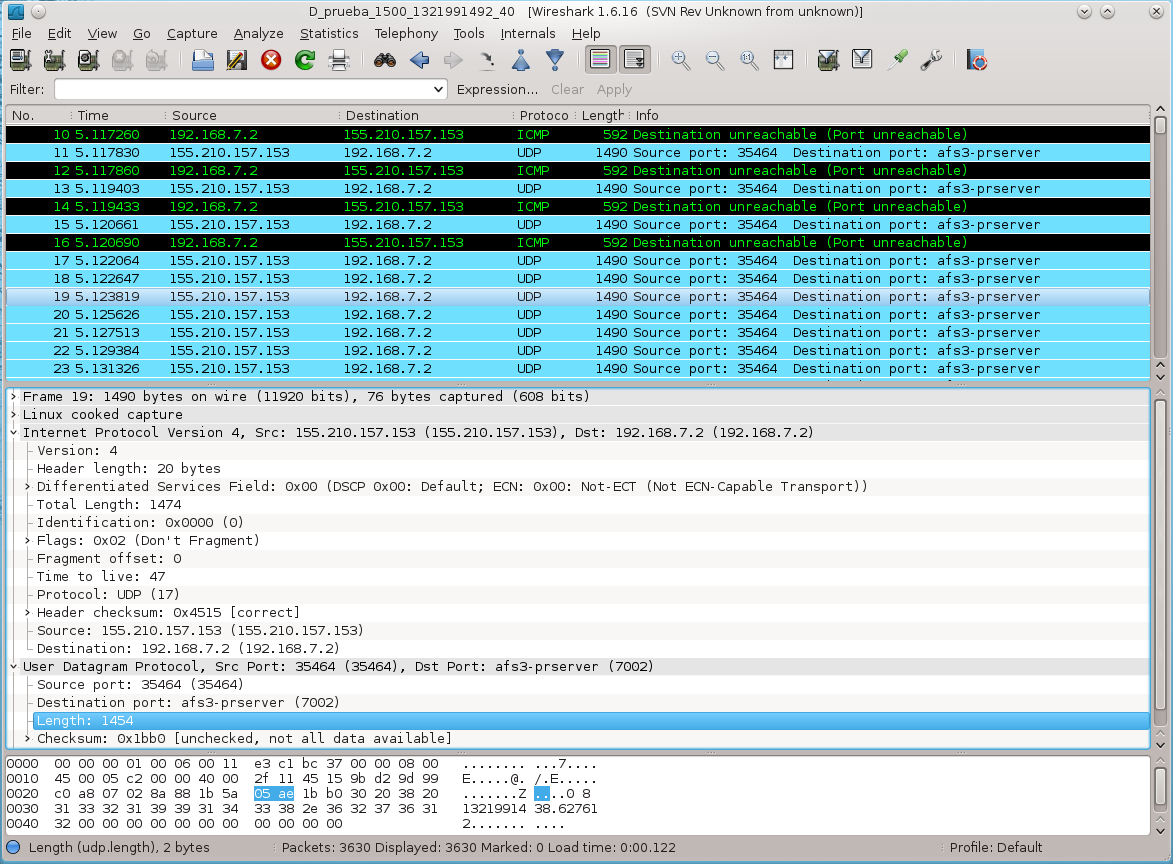
The 2 best tools for the capture and the interpretation of network data
The applications to capture packets on the network, e.g. tcpdump and wireshark are well known for their features, in addition to data capture, these applications are useful for certain packets analysis with the obtained data.